Linux makes it easy to encrypt and decrypt files using the “gpg” utility that’s included by default in just about every installation. The package is an open source implementation of a tool previously used by Symantec, and which has even received a chunk of funding from the German government.
In this article, I’ll show you a few quick commands to easily encrypt a file using a passphrase.
Encrypting Files
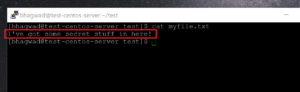
“GNU Privacy Guard” is the full form of “gpg“, and you can get started with encrypting files immediately. In this screenshot for example, I have a sample file with some random content:
I can encrypt it using the following command:
gpg -c myfile.txt
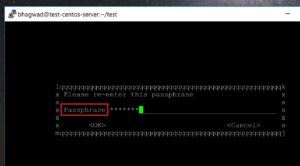
This will open up a dialogue box asking for a password. Once you enter the password, you’ll be asked to retype it again to confirm:
That’s it. You’re done! If you look at the original location of the file, you’ll now see another file with the “.gpg” extension like this:
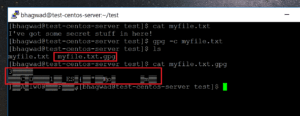
This contains the encrypted data. You can verify this by opening it and taking a look at the contents as shown above. The output is nothing but junk.
[su_note note_color=”#f5f5d4″ radius=”6″]| Also Read | Top Linux Distros 2018[/su_note]
What to Do with the Encrypted File?
Once you have both the original and the encrypted file, you have two options:
- Either delete the original from your hard disk
- Mail the encrypted file to someone else
The first is so that you can hide sensitive data on your own personal system. The second option is to be able to send someone the encrypted version of the file in a secure manner without anyone looking at it. It’s a great way to share sensitive information.
You need to communicate the passphrase that you generated in the first step. This can be over an unrelated medium like the phone for example. Obviously you don’t want to use the same channel over which you send the encrypted file!
[su_note note_color=”#f5f5d4″ radius=”6″]| Also Read | Terminology Basics you need to know[/su_note]
Decrypting the File
Once you have the encrypted file in your hands, it’s time to decrypt it. You can do this using the following command:
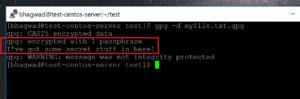
gpg -d myfile.text.gpg
However, if you run this command on your own system immediately after encrypting the file, gpg won’t ask you for the password and the contents will be displayed on the screen like this:
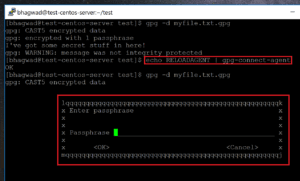
This is because the “gpg-agent” process has cached the password you just used and won’t ask you for it again in a certain time frame. We can temporarily bypass this by reloading the agent like this:
echo RELOADAGENT | gpg-connect-agent
This time, it asks you for the password when you try and decrypt:
You can make behavior permanent by editing this file:
~/.gnupg/gpg-agent.conf
And adding the following lines:
default-cache-ttl 1
max-cache-ttl 1
This sets the expiry of the cache to 1 second.
Note that the decryption dumps the file data onto the screen. If you want, you can send the output to a file using the “-o” parameter as shown here:
gpg -o newfile.txt -d myfile.txt.gpg
[su_note note_color=”#f5f5d4″ radius=”6″]| Also Read | Types of Programming Difference you need to Know[/su_note]
Using More Secure Encryption Methods
In the screenshots above, you might have noticed the following message while decrypting:
WARNING: Message was not integrity protected
This means that gpg cannot be sure that the encrypted file has not been tampered with. It’s because by default, gpg uses an older CAST5 encryption protocol. However, newer encryption methods have since been devised that protect against file tampering. The AES protocol for example, is much more secure.
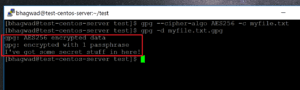
We can force gpg to use 256-bit AES encryption with the following parameter:
--cipher-algo AES256
So the encryption command becomes:
gpg --cipher-algo AES256 -c myfile.txt
This time when we decrypt, we no longer get the warning:
Even more secure would be to sign the file with your keypair. But that’s for another tutorial!
This post is a Guest from Jeff Wilson from Linux Host Support
Jeff Wilson is a senior Linux system administrator at LinuxHostSupport, a premium server management company that focus on Linux server administration.
If anyone of readers want to share a guest post, he can also do via link Guest-posting Link . Stay connected for more updates coming up next. This one was well 99th post of our blog, We will be starting something new from our 100th post , so stay connected and keep checking.








Attractive section of content. I just stumbled upon your blog and in accession capital to assert that I acquire in fact enjoyed account your blog posts. Anyway I’ll be subscribing to your feeds and even I achievement you access consistently fast.|
Thanks
Hey there, You’ve done an incredible job. I’ll certainly digg it and personally recommend to my friends. I’m confident they’ll be benefited from this website.|
Thanks
Hi there to every one, the contents existing at this website are genuinely remarkable for people knowledge, well, keep up the nice work fellows.|
Thanks
Hi there! Someone in my Myspace group shared this site with us so I came to check it out. I’m definitely loving the information. I’m book-marking and will be tweeting this to my followers! Fantastic blog and fantastic design.|
Thanks
You actually make it seem so easy with your presentation however I in finding this topic to be actually something which I think I’d by no means understand. It seems too complex and very extensive for me. I am taking a look ahead for your subsequent put up, I will attempt to get the hold of it!|
Thanks, keep visiting