Let’s understand Embedded Analytics
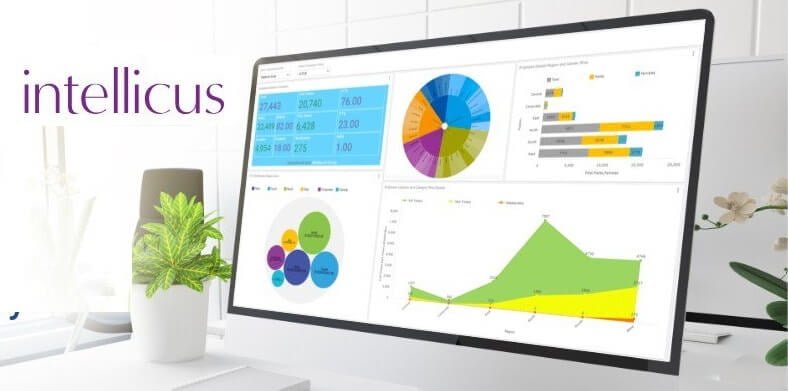
Embedded analytics is nothing more than a specific technique for applying the tools of business intelligence to your data. The difference between embedded analytics and traditional BI is basically just the context in which data gets analyzed and scrutinized.
[su_note note_color=”#f5f5d4″ radius=”6″]| Also Read | Softwares for Building websites in Minutes[/su_note]
Embedded analytics integrates the capabilities of a stand-alone BI platform into a franchise’s own systems and applications. In other words, embedded analytics provide users with the ability to get to the data analysis they need from within the software they already use.
Most users don’t typically need to get a high-level perspective of all the business data, nor would they want to. They also would prefer not to have to navigate between the software they typically use and some separate BI tool. Users like the efficiency and ease of use that embedded analytics delivers to help them comprehend their specific data and gain insights for making better data-based decisions.
Security is a Major Concern for Protecting Your Customer’s or Client’s Data
When you’re structuring data viewpoints for a product, the security of the data in question is exceptionally vital. Several features allow you to procure specific data, such that clients can see only that data (and resulting analysis) which you intend for them to see. You can see why security is vital at this juncture; and you can’t risk client A, accidentally getting a glimpse of client B’s data!
Every user project you create on the software has both user management and consumer access capabilities. Additionally, the ability to safeguard your queries via access keys which refine your data views offered by the software dashboard.
[su_note note_color=”#f5f5d4″ radius=”6″]| Also Read | Types of System Integration[/su_note]
Embedded Analytics Security Solutions
When it comes to embedded analytics programs, keeping your data secure is crucial. Embedded analytics utilizes a variety of security features. These features focus on maintaining your proprietary data and keeping it out of harm’s way. For starters, it’s vital to limit the level of individual user access by role-based criteria. This guarantees that only the appropriate people have access to specific data or features, and decreases the chances of inadvertent leaks.
The Embedded analytics may also keep a list of user and administrative activities through activity monitoring. Supervisors can generate a report on these activities to observe where the origin of the problem lies, should an issue arise.
Before users can access any functionality, embedded analytics provide single-sign-on attributes which necessitate authentication tickets from the server application. This allows users to obtain the integrated BI solution inside the server program without being required to log in separately, eliminating unnecessary steps.
Essential Security Features of Embedded Analytics Tools:
- Role and User-Based Access
- Application Activity Monitoring
- Single Sign-On
- Trusted Verification
- Row/Column Level Security
- User Filtering
- Integrated Security
[su_note note_color=”#f5f5d4″ radius=”6″]| Also Read | 5 Best Apps for programming studenst[/su_note]
Platforms Powered by Embedded Analytics and AI in 2019
With hybrid cloud options for embedded analytics gaining popularity in 2019. thanks in part to more decentralized information flowing throughout organizations – security will continue to be an even more widespread concern. Safety for embedded analytics in particular, as well as for BI in general, will have to be very adaptive.
Companies will need to start implementing protected keys and authentications for APIs (Application Programming Interfaces), as well as consumer authentications and permissions. It will also be imperative for these companies to embrace a flexible security architecture that supports mobile devices to embrace the present and future of business fully.
[su_note note_color=”#f5f5d4″ radius=”6″]| Also Read | A new Book in the Hood – JS Grammar[/su_note]
Adaptive Security Mechanisms in 2019:
Introducing more safety features into a system brings many positive impacts, but this doesn’t come without its share of associated costs. Keeping this fact in mind is essential in the design of effective embedded BI systems in forums which may be limited in the scope of available resources.
Therefore, it is essential to do a trade-off analysis between non-functional necessities to create a necessary equilibrium between them.
This tactic permits the system to embrace either a more or less time-consuming encryption algorithm, depending on the results provided by previous executions of encryption procedures. This is particularly important for systems having a higher degree of sophistication, which is sometimes difficult to analyze mathematically.
For more information about the most effective embedded analytics tools available for businesses today, be sure to check out the BI solutions provided by the Intellicus.
[su_note note_color=”#f5f5d4″ radius=”6″]| Also Read | Top 10 Emerging Technologies in Computer Science[/su_note]
Hope you all like the post, feel free to share your comments below. Thanks for reading, please keep visiting back for more awesome stuff coming next.